Enhanceble Compliance
In order to provide an environment to built compliant applications, Dchain provides Verifiable Credential Verification (VCV) at the time of transaction and the verification requirements are tailored to the type of transactions performed by users and validators. This granular, real time and un-opinionated design allows for scalable trust and identity framework to be used.
It is important to note that no credential data is provided to the chain, only the derived presentations, credentials are always stored safely by the user offchain (optionally with their chosen SSI agent).
There are 3 layers where verifiable credential verification (VCV) is performed on Dchain:
- Consensus: On block proposal, block processing and voting, validators provide their Verifiable Presentations which are verified by others. The presentation must be derived from a credential issued by one of the entities determined by the chain's governance.
- Dchain level wide: The Dchain governance defines the presentation requirements to execute certain messages on the chain. (See gov for more details).
- Business Application Specific: The application can define their own verification requirements and the chain will enforce them.
Consensus level credential verification
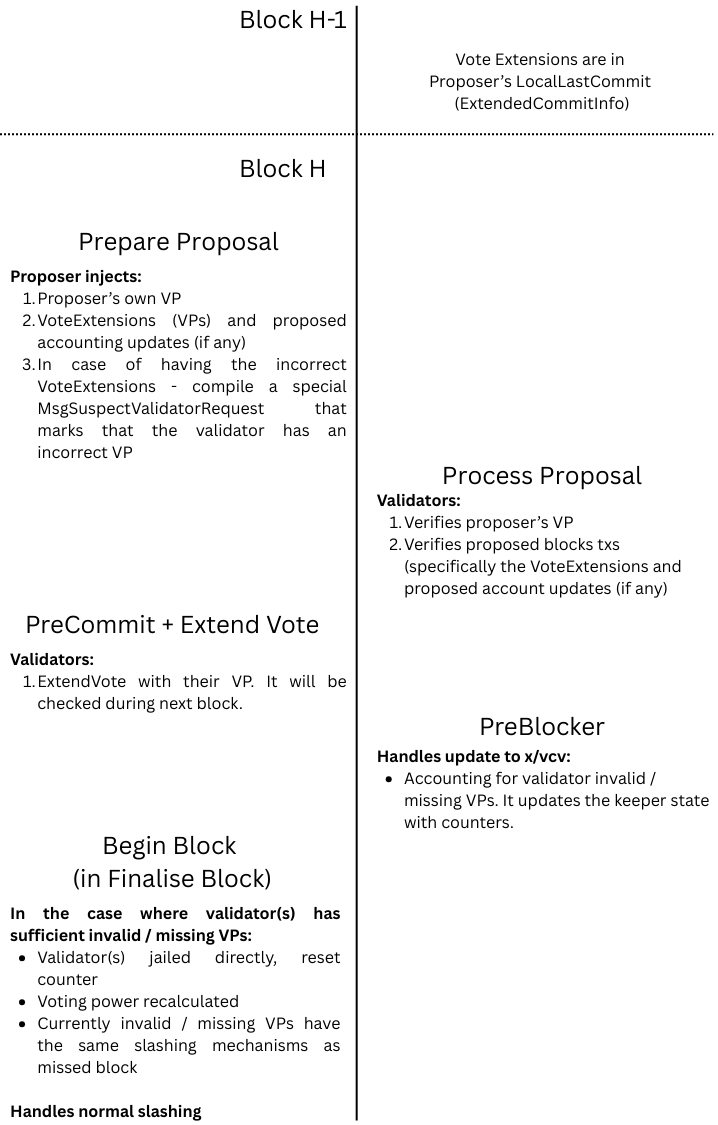
Dchain utilises ABCI 2.0 methods to allow CometBFT and the Application (Dchain Application Layer) to interact at different stages of the block proposal and validation process.
VP are required to do block proposal (by the proposer) and as a part of extended vote data (by the validators). Below is the high level flow:
Validator Onboarding
Example of this can be seen in the testnet instructions.
Dchain validators are required to be onboarded by one of the trusted issuers to obtain a valid verifiable credential. The group of trusted issuers and onboarding criteria are determined by the chain's governance rules and can be updated by the governance process. Verifiable credentials can expire and it can also be revoked by the chain's governance.
This extra relation with validators provide high level of commitment from validators as their votes on blocks containing both onchain state transition data and their verfiable .
Furthermore, for certain classification of cryptoassets such as BIS classification of Group 1 cryptoassets, it is expected that all "All entities that execute redemptions, transfers, storage or settlement of the cryptoasset, must: (i) be regulated and supervised, or subject to appropriate risk management standards; and (ii) have in place and disclose a comprehensive governance framework".
Dchain delivers a network that uses SSI for consensus participants, to support all sorts of cryptoassets and regulatory grade decentralised applications.
Each validator is a verifiable credential holder, and are required to selective disclose attributes as verifiable presentation (VP) to the network.
The other validators against governance defined requirements, such as who issued it and if it has been revoked or not. Any violation will result in a reject vote. If of voting power where rejects, it will result in rejection of the block.
Application Specific Verification Requirements
For applications deployed on Dchain, they can register multiple routes (each mapping to specific state transition message) with the chain's VCV module.
As part of the chain's transaction verification process (which typically only handles signature verification), the chain invokes the VCV module will verify the user's presentation against the application's defined requirements.
This allows the application to fully control and enforce the verification requirements.
Supported Verifiable Credential Presentation Formats
Dchain currently supports the following verifiable credential presentation formats:
- AnonCreds: Zero Knowledge Proof based presentation verification (soon)
- SD-JWT: Selective Disclosure JWT based presentation verification
These formats are selected for their compatibility with adopted SSI standards, such as European Digital Identity (EUDI) regulations.
Prior Work
The AVIDA - Atomic Verification of Identity for Decentralised Applications protocol is an open source project developed by NYMLAB to provide decentralised applications on blockchains to easily add verification requirements for their users.
This allows developers to focus on their application logic and not worry about the complexities verifiable credentials verification and getting updated trusted issuer data over IBC.
Dchain implements the this protocol on the chain level.